Describe Five Best Practices When Implementing a Wireless Network
The best option is to enable it tweak it test it as per your requirements and then disable it. List at least six security best practices that you should implement to secure your multi-function device and wireless network.
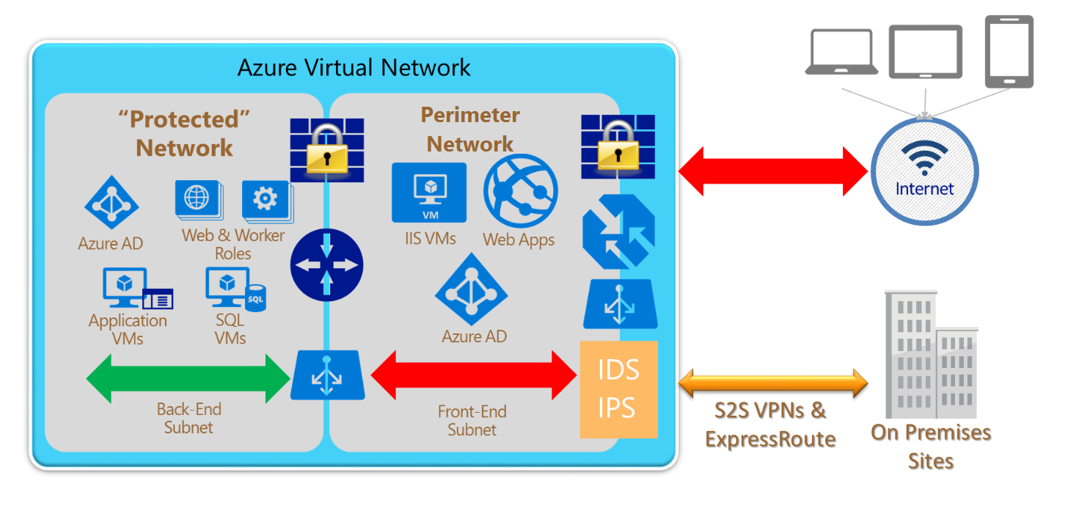
Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs
The International Organization for Standardization ISO network management model defines five functional areas of network management.

. The inevitable moves additions. 5 Best Practices for Implementing a New Wireless Network 1. Each wireless device in the network should have a minimum of three other devices with potential communication paths.
All that the CCNA staff need do is properly set up the site for use. Use Separate Policy Enforcement and Context Variables to Tailor Guest Access to Individual Needs. Establish Formal Registration Processes to Control Access to Guest Networks.
The overall purpose of this document is to provide practical recommendations on each functional area to increase the overall effectiveness of current management tools and practices. Network segmentation is a best practice that can help to reduce the damage caused by a malware or ransomware attack. Have a rogue detection process capability.
Use BestinClass Security to Protect the WLAN and Intellectual Property 5. Plan and Build a Robust ForwardLooking WLAN 2. Provide Services for Each Class of User 4.
Have a rogue WAP detection capability. Wi-Fi networks dont stay in top condition on their own. Use Centralized Management 3.
1 Change default values for the SSID usernames and passwords 2 Disable broadcast SSID 3 Configure MAC Address Filtering 4 Configure encryption using WEP or WPA 5 Configure authentication 6. Contents 1 Executive Overview 2 Background 3 Best Practices 1. As per the wireless use policy.
Segmentation of Wi-Fi users and devices by SSID. To achieve this it is recommended that a minimum of five wireless devices are within effective range of each gateway. It will also help ensure the most important bandwidth is reserved for the most critical operations.
Push out antivirus software upgrades to clients from servers. WAP detection capability should reliably detect the presence of a WAP communicating inside the physical perimeter of the enterprise. Without a thought out wireless network management policy in place your enterprise cant expect its wireless network to run properly.
Rate limit clients on the Guest WLAN using applications like YouTube iTunes etc. Deployment planning installation and management of the wireless equipment. Deploy a network-based intrusion-detection system on the wireless network.
The world of wireless changed dramatically in 2003 when Airespace later acquired. Use Content Filtering and Bandwidth Limiting to Control Content That Will Be Accessed and Viewed in the Enterprise Environment. Part of an effective wireless management strategy is implementing a series of best practices that help your enterprise effectively manage their network.
Memory can be finicky. Carry Out a Policy Based on Guest Access Roles. Use and maintain antivirus software.
Segregating wireless channels for employees IoT devices and visitorscustomers with a virtual LAN for example will make the network more manageable and provide a layer of security. The focus of this how-to tutorial is on a typical wireless extension to a wired local area network in an. Use managed wireless products.
Set up a separate guest Wi-Fi SSID for those users and devices that only require internet access. If a computer is compromised attackers will attempt to more laterally and access other devices and parts of the network. Network management is essentially the process of setting up administering and troubleshooting a network whether for home or business purposesThe purpose of network management is to ensure that the IT side of a business is set up in a resilient sensible way which can minimize disruptions ensure high performance and help you avoid security issues.
It is assumed that the site has already been deemed appropriate for a wireless network. It majorly depends on the need of the clients so set the protocol accordingly. Workstation simultaneously broadcasting IP from a second wireless network interface card NIC.
Other best practices include the following. Or you can enable a WEP WPA AND WPA2 protocol in the AP to password protect the network. Consider application throughput requirements specially for voice and video.
Best Practices 2 of 14 Share. This document covers all functional areas. If no security protocol is enabled then anyone can join the network.
Departments and devices use WLANs in different ways. The security of the network depends on the settings of the APs.

Ccna 3 V7 Modules 3 5 Network Security Exam Answers

Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

Hotel Wifi Network Design Best Practices And Installation Strategies Blueprint Rf
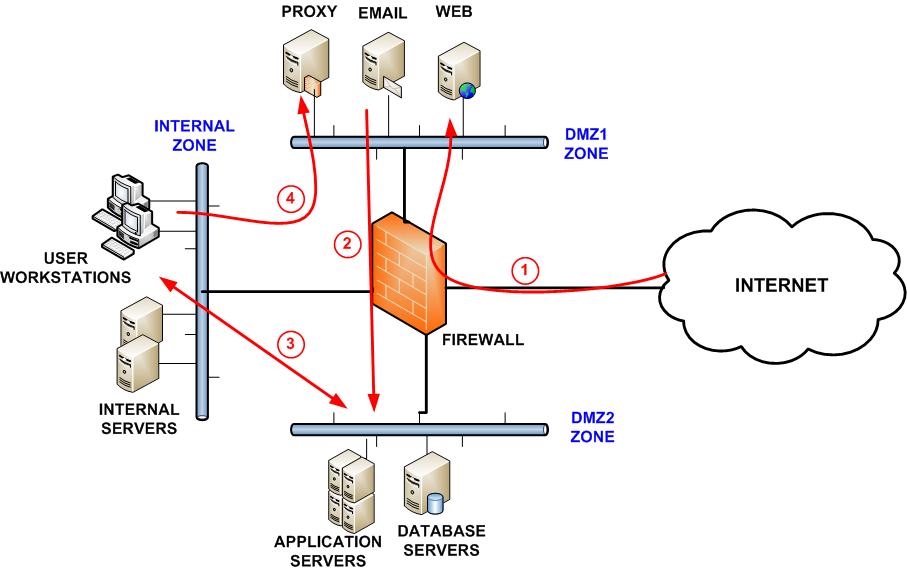
Network Segmentation Best Practices To Improve Security Web Filtering

Home Network Segmentation A Must In The Iot Era Between The Hacks

Webinar Networking Design And Best Practices Youtube

10 Best Practices For Email Security In 2021 Titanfile
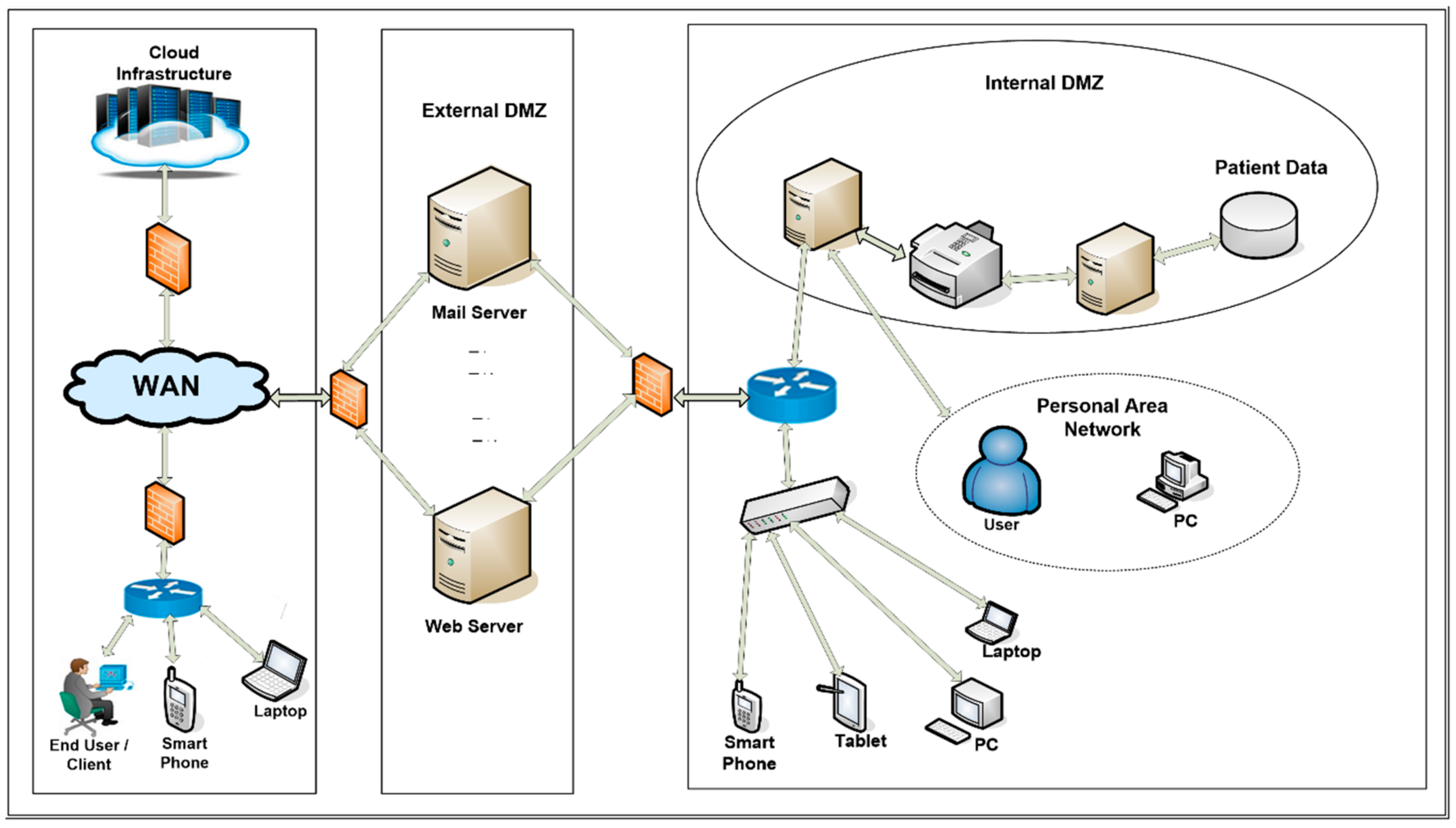
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

The 4 Best Practices For Wifi Network Security Jumpcloud Jumpcloud

The 4 Best Practices For Wifi Network Security Jumpcloud Jumpcloud
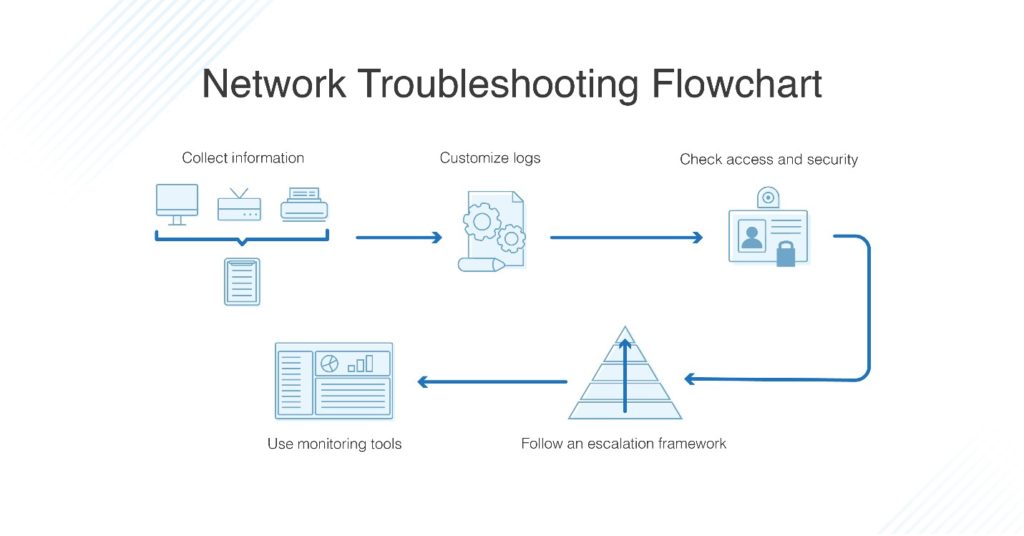
Network Troubleshooting Steps Techniques Best Practices Dnsstuff
7 Data Loss Prevention Best Practices Expert Explains Purplesec

Ways To Secure Your It Network Infographic Networking Infographic Cyber Security Education Computer Security
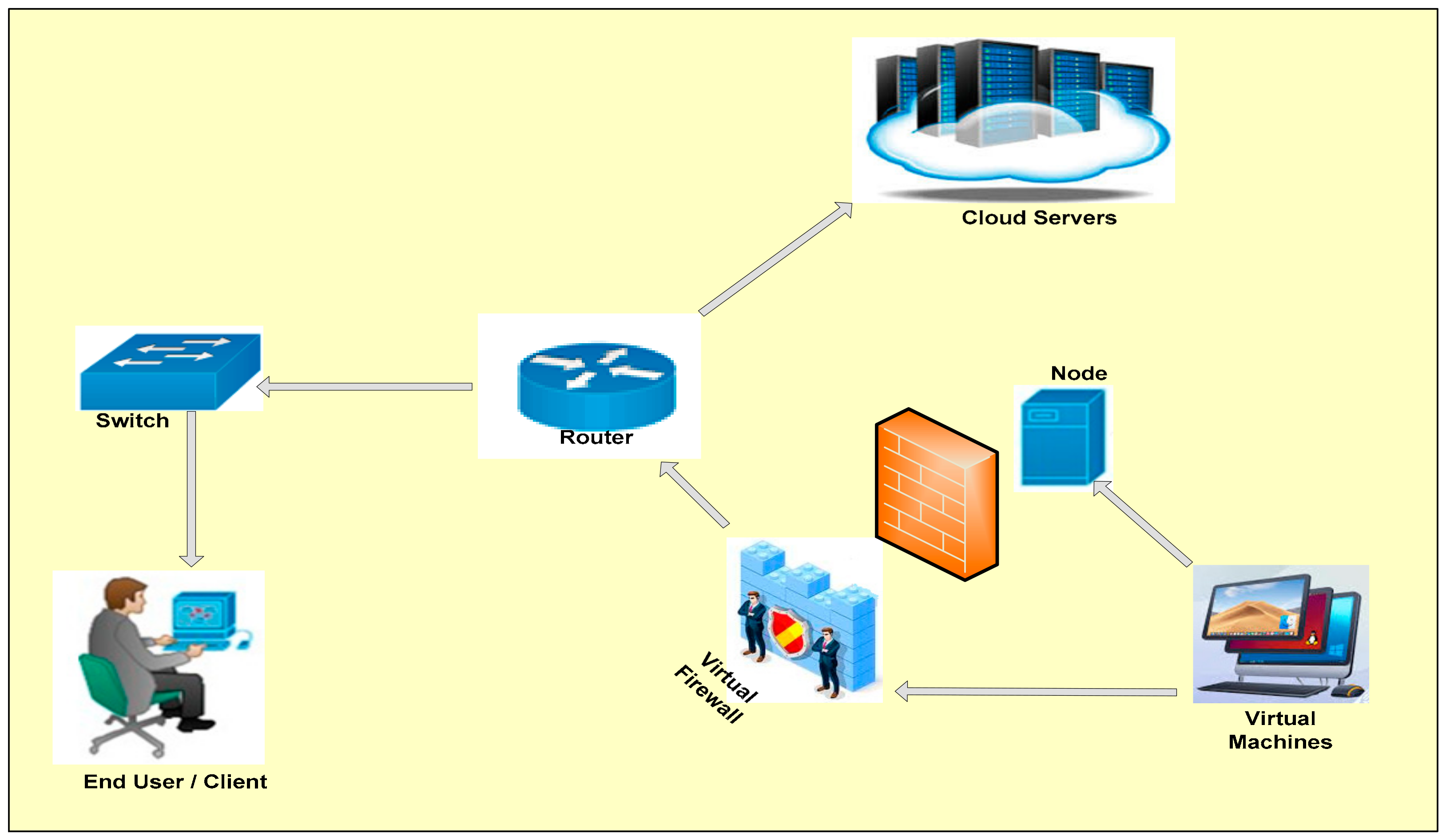
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
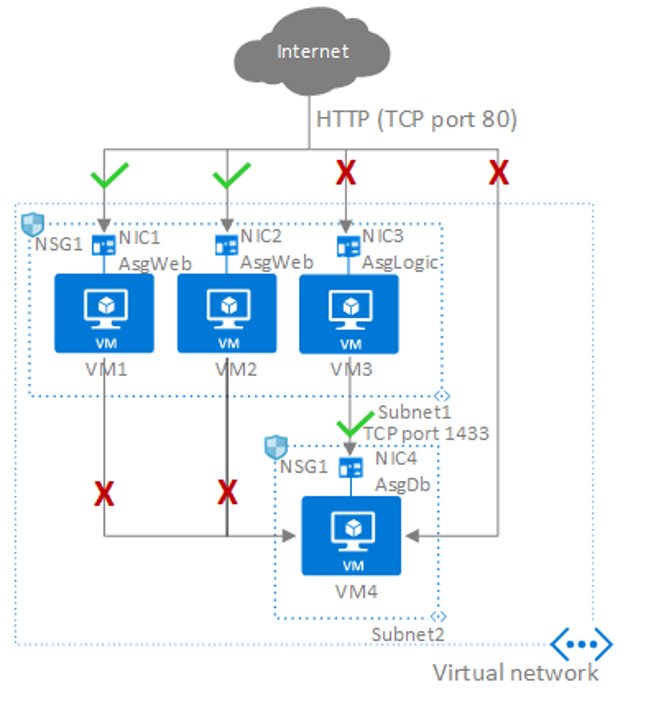
Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

Wireless Access Security Policy Best Practices Information Security Program
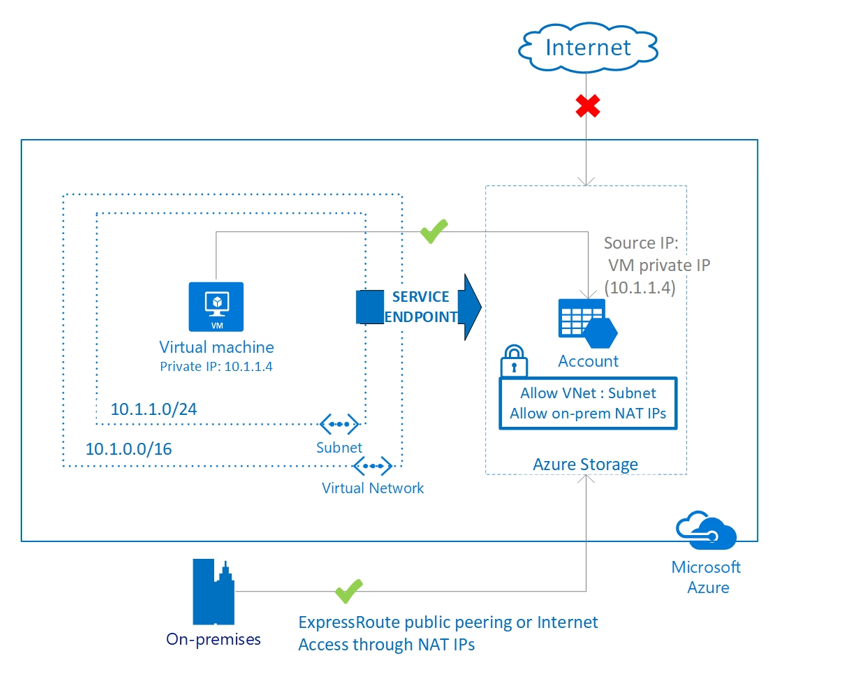
Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

Comments
Post a Comment